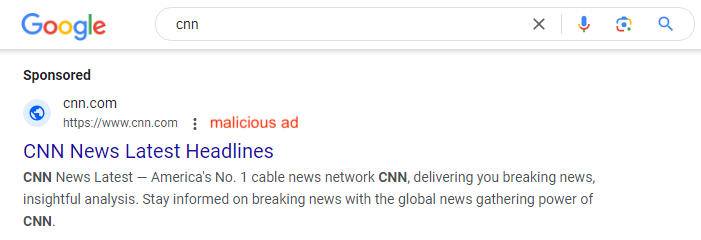
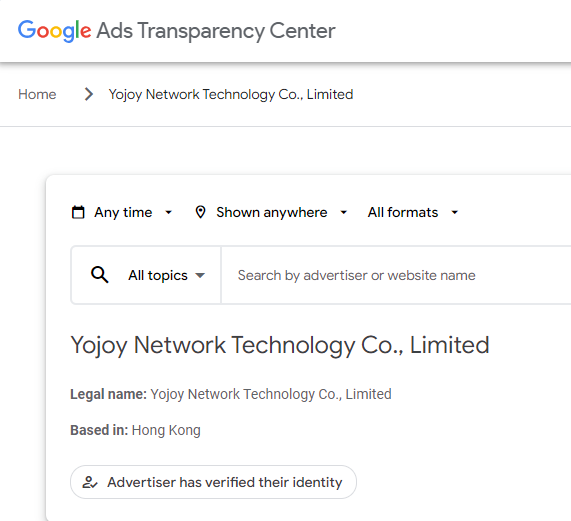
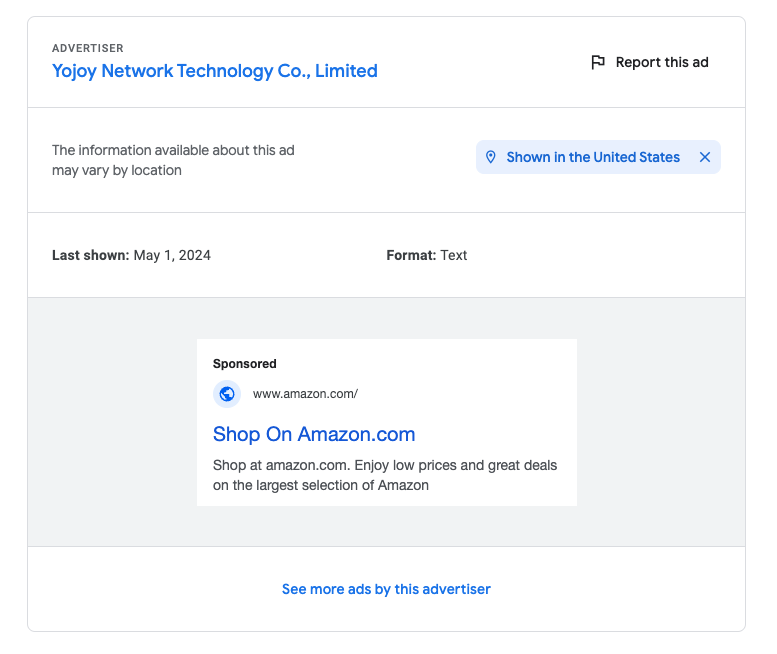
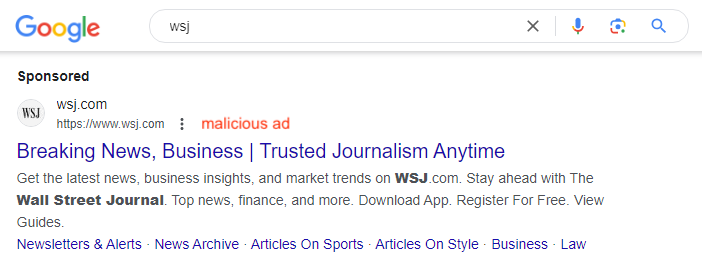
This interview is crossposted from The Markup, a nonprofit news organization that investigates technology and its impact on society.
By: Monique O. Madan, Investigative Reporter at The Markup

After reading my daily news stories amid his declining health, my grandfather made it a habit of traveling the world—all from his desk and wheelchair. When I went on trips, he always had strong opinions and recommendations for me, as if he’d already been there. “I've traveled to hundreds of countries," he would tell me. "It's called Google Earth. Today, I’m going to Armenia.” My Abuelo’s passion for teleporting via Google Street View has always been one of my fondest memories and has never left me.
So naturally, when I found out that Dave Maass of the Electronic Frontier Foundation gave virtual reality tours of surveillance technology along the U.S.–Mexico border, I had to make it happen. I cover technology at the intersection of immigration, criminal justice, social justice and government accountability, and Maass’ tour aligns with my work as I investigate border surveillance.
My journey began in a small, quiet, conference room at the Homestead Cybrarium, a hybrid virtual public library where I checked out virtual reality gear. The moment I slid the headset onto my face and the tour started, I was transported to a beach in San Diego. An hour and a half later, I had traveled across 1,500 miles worth of towns and deserts and ended up in Brownsville, Texas.
During that time, we looked at surveillance technology in 27 different cities on both sides of the border. Some of the tech I saw were autonomous towers, aerostat blimps, sky towers, automated license plate readers, and border checkpoints.
After the excursion, I talked with Maass, a former journalist, about the experience. Our conversation has been edited for brevity and clarity.
Monique O. Madan: You began by dropping me in San Diego, California, and it was intense. Tell me why you chose the location to start this experience.
Dave Maass: So I typically start the tour in San Diego for two reasons. One is because it is the westernmost part of the border, so it's a natural place to start. But more importantly, it is such a stark contrast to be able to jump from one side to the other, from the San Diego side to the Tijuana side.
When you're in San Diego, you're in this very militarized park that's totally empty, with patrol vehicles and this very fierce-looking wall and a giant surveillance tower over your head. You can really get a sense of the scale.
And once you're used to that, I jump you to the other side of the wall. You're able to suddenly see how it's party time in Tijuana, how they painted the wall, and how there are restaurants and food stands and people playing on the beach and there are all these Instagram moments.

Credit: Electronic Frontier Foundation
Yet on the other side is the American militarized border, you know, essentially spying on everybody who's just going about their lives on the Mexican side.
It also serves as a way to show the power of VR. If there were no wall, you could walk that in a minute. But because of the border wall, you've got to go all the way to the border crossing, and then come all the way back. And we're talking, potentially, hours for you to be able to go that distance.
Madan: I felt like I was in two different places, but it was really the same place, just feet away from each other. We saw remote video surveillance systems, relocatable ones. We saw integrated fixed towers, autonomous surveillance towers, sky towers, aerostat radar systems, and then covert automated license plate readers. How do you get the average person to digest what all these things really mean?
7 Stops on Dave Maass’ Virtual Reality Surveillance Tour of the U.S.–Mexico Border
The following links take you to Google Street View.
|
Maass: Me and some colleagues at EFF, we were looking at how we could use virtual reality to help people understand surveillance. We came up with a very basic game called “Spot the Surveillance,” where you could put on a headset and it puts you in one location with a 360-degree camera view. We took a photo of a corner in San Francisco that already had a lot of surveillance, but we also Photoshopped in other pieces of surveillance. The idea was for people to look around and try to find the surveillance.
When they found one, it would ping, and it would tell you what the technology could do. And we found that that helped people learn to look around their environment for these technologies, to understand it. So it gave people a better idea of how we exist in the environment differently than if they were shown a picture or a PowerPoint presentation that was like, “This is what a license plate reader looks like. This is what a drone looks like.”
That is why when we're on the southern border tour, there are certain places where I don't point the technology out to you. I ask you to look around and see if you can find it yourself.
Sometimes I start with one where it's overhead because people are looking around. They're pointing to a radio tower, pointing to something else. It takes them a while before they actually look up in the sky and see there's this giant spy mob over their head. But, yeah, one of the other ones is these license plate readers that are hidden in traffic cones. People don't notice them there because they're just these traffic cones that are so ubiquitous along highways and streets that they don't actually think about it.
Madan: People have the impression that surveillance ops are only in militarized settings. Can you talk to me about whether that’s true?
Maass: Certainly there are towers in the middle of the desert. Certainly there are towers that are in remote or rural areas. But there are just so many that are in urban areas, from big cities to small towns.
Rather than just a close-up picture of a tower, once you actually see one and you're able to look at where the cameras are pointed, you start to see things like towers that are able to look into people's back windows, and towers that are able to look into people's backyards, and whole communities that are going to have glimpses over their neighborhood all the time.
But so rarely in the conversation is the impact on the communities that live on both the U.S. and Mexican side of the border, and who are just there all the time trying to get by and have, you know, the normal dream of prospering and raising a family.
Madan: What does this mean from a privacy, human rights, and civil liberties standpoint?
Maass: There’s not a lot of transparency around issues of technology. That is one of the major flaws, both for human rights and civil liberties, but it's also a flaw for those who believe that technology is going to address whatever amorphous problem they've identified or failed to identify with border security and migration. So it's hard to know when this is being abused and how.
But what we can say is that as [the government] is applying more artificial intelligence to its camera system, it's able to document the pattern of life of people who live along the border.
It may be capturing people and learning where they work and where they're worshiping or who they are associated with. So you can imagine that if you are somebody who lives in that community and if you're living in that community your whole life, the government may have, by the time you're 31 years old, your entire driving history on file that somebody can access at any time, with who knows what safeguards are in place.
But beyond all that, it really normalizes surveillance for a whole community.
There are a lot of psychological studies out there about how surveillance can affect people over time, affect their behavior, and affect their perceptions of a society. That's one of the other things I worry about: What kind of psychological trauma is surveillance causing for these communities over the long term, in ways that may not be immediately perceptible?
Madan: One of the most interesting uses of experiencing this tour via the VR technology was being able to pause and observe every single detail at the border checkpoint.
Maass: Most people are just rolling through, and so you don't get to notice all of the different elements of a checkpoint. But because the Google Street View car went through, we can roll through it at our leisure and point out different things. I have a series of checkpoints that I go through with people, show them this is where the license plate reader is, this is where the scanner truck is, here's the first surveillance camera, here's the second surveillance camera. We can see the body-worn camera on this particular officer. Here's where people are searched. Here's where they're detained. Here's where their car is rolled through an X-ray machine.
Madan: So your team has been mapping border surveillance for a while. Tell us about that and how it fits into this experience.
Maass: We started mapping out the towers in 2022, but we had started researching and building a database of at least the amount of surveillance towers by district in 2019.

I don't think it was apparent to anyone until we started mapping these out, how concentrated towers are in populated areas. Maybe if you were in one of those populated areas, you knew about it, or maybe you didn't.
In the long haul, it may start to tell a little bit more about border policy in general and whether any of these are having any kind of impact, and maybe we start to learn more about apprehensions and other kinds of data that we can connect to.
Madan: If someone wanted to take a tour like this, if they wanted to hop on in VR and visit a few of these places, how can they do that?
Maass: So if they have a VR headset, a Meta Quest 2 or newer, the Wander app is what you're going to use. You can just go into the app and position yourself somewhere in the border. Jump around a little bit, maybe it will be like five feet, and you can start seeing a surveillance tower.
If you don’t have a headset and want to do it in your browser, you can go to EFF’s map and click on a tower. You’ll see a Street View link when you scroll down. Or you can use those tower coordinates and then go to your VR headset and try to find it.
Madan: What are your thoughts about the Meta Quest headset—formerly known as the Oculus Rift—being founded by Palmer Luckey, who also founded the company that made one of the towers on the tour?
Maass: There’s certainly some irony about using a technology that was championed by Palmer Luckey to shine light on another technology championed by Palmer Luckey. That's not the only tech irony, of course: Wander [the app used for the tour] also depends on using products from Google and Meta, both of whom continue to contribute to the rise of surveillance in society, to investigate surveillance.
Madan: What's your biggest takeaway as the person giving this tour?
Maass: I am a researcher and educator, and an activist and communicator. To me, this is one of the most impactful ways that I can reach people and give them a meaningful experience about the border.
I think that when people are consuming information about the border, they're just getting little snippets from a little particular area. You know, it's always a little place that they're getting a little sliver of what's going on.
But when we're able to do this with VR, I'm able to take them everywhere. I'm able to take them to both sides of the border. We're able to see a whole lot, and they're able to come away by the end of it, feeling like they were there. Like your brain starts filling in the blanks. People get this experience that they wouldn't be able to get any other way.
Being able to linger over these spaces on my own time showed me just how much surveillance is truly embedded in people's daily lives. When I left the library, I found myself inspecting traffic cones for license plate readers.
As I continue to investigate border surveillance, this experience really showed me just how educational these tools can be for academics, research and journalism.
Thanks for reading,
Monique
Investigative Reporter
The Markup
This article was originally published on The Markup and was republished under the Creative Commons Attribution-NonCommercial-NoDerivatives license.




 Sachin Tendulkar Deepfake Scam (Source: X)[/caption]
Sachin Tendulkar Deepfake Scam (Source: X)[/caption]
 Anant Ambani Deepfake (Source: The Quint)[/caption]
Anant Ambani Deepfake (Source: The Quint)[/caption]







 The DFINITY Foundation is a Swiss-based not-for-profit organization known for its innovative approach to blockchain technology. It operates a web-speed, internet-scale public platform that enables smart contracts to serve interactive web content directly into browsers. This platform supports the development of decentralized applications (dapps), decentralized finance (DeFi) projects, open internet services, and enterprise systems capable of operating at hyper-scale.
On the other hand, Cryptonary is a leading platform in the crypto tools and research space. It provides essential insights and analysis to help users navigate the complexities of the cryptocurrency market and capitalize on emerging opportunities.
When The
The DFINITY Foundation is a Swiss-based not-for-profit organization known for its innovative approach to blockchain technology. It operates a web-speed, internet-scale public platform that enables smart contracts to serve interactive web content directly into browsers. This platform supports the development of decentralized applications (dapps), decentralized finance (DeFi) projects, open internet services, and enterprise systems capable of operating at hyper-scale.
On the other hand, Cryptonary is a leading platform in the crypto tools and research space. It provides essential insights and analysis to help users navigate the complexities of the cryptocurrency market and capitalize on emerging opportunities.
When The  Source: Offical Website of The DFINITY Foundation[/caption]
While this message serves as a caution regarding phishing scams, it is unclear whether it hints at a broader security issue or is merely a general warning. The DFINITY website and the Cryptonary website both appeared fully functional with no evident signs of compromise.
The Cyber Express Team reached out to the officials of both companies for verification of the breach claims. However, as of the time of writing, no official response had been received, leaving the authenticity of the threat actor's claims unverified.
Now whether this message is a hint that they are being attacked by a criminal or it's just a caution message, we can come to the conclusion they release any official statement regarding the same.
Source: Offical Website of The DFINITY Foundation[/caption]
While this message serves as a caution regarding phishing scams, it is unclear whether it hints at a broader security issue or is merely a general warning. The DFINITY website and the Cryptonary website both appeared fully functional with no evident signs of compromise.
The Cyber Express Team reached out to the officials of both companies for verification of the breach claims. However, as of the time of writing, no official response had been received, leaving the authenticity of the threat actor's claims unverified.
Now whether this message is a hint that they are being attacked by a criminal or it's just a caution message, we can come to the conclusion they release any official statement regarding the same.