
Microsoft’s cybersecurity efforts have been roundly criticized in recent months, and despite pledges to do better, the company has compounded the problem with missteps like the Copilot+ Recall rollout.
Microsoft security controls came under scrutiny in April with the release of a U.S. Cyber Safety Review Board (CSRB)
report that detailed “a cascade of security failures at Microsoft” that allowed threat actors linked to China to access “the official email accounts of many of the most senior U.S. government officials managing our country’s relationship with the People’s Republic of China” in a
July 2023 attack.
Rather than make good on
pledges to make cybersecurity a top priority, Microsoft followed with the cybersecurity equivalent of an own goal when it pushed ahead with the new Windows Recall screen recording feature despite the
concerns of security and privacy advocates that the company
belatedly tried to address. Late today, Microsoft
announced that it will delay the Recall feature for further testing.
The House Committee on Homeland
Security held a hearing today to address the CSRB report and Microsoft security in general, with Microsoft President Brad Smith the sole witness. The hearing, titled “A Cascade of Security Failures: Assessing Microsoft Corporation’s Cybersecurity Shortfalls and the Implications for Homeland Security,” came on the same day that Pro Publica published a report detailing
years of Microsoft security failings that led up to the massive 2021 SolarWinds breach.
Congressional Leaders Call for ‘Responsibility’ and ‘Accountability’
In his opening remarks, House Homeland Security Chairman Mark Green (R-TN) called the CSRB report “extremely concerning,” and spoke of the need of “restoring the public trust” in the security of Microsoft products.
“China and Russia, Beijing and Moscow, are watching us right now,” he cautioned, underscoring the stakes of the hearing while offering to move any sensitive questions to a secure environment.
Ranking member Bennie Thompson (D-MS) stressed that “It is not the committee’s goal to shame or discredit” Smith and Microsoft, but to improve security and accountability at the vendor that supplies 85% of federal government productivity tools.
Thompson noted the Recall rollout and Pro Publica article in his comments, calling “even more troubling” Smith’s 2021 claim before Congress that no Microsoft vulnerability was exploited in the SolarWinds attack.
Green and Thompson weren’t the only committee members taking a firm tone with Microsoft, as almost every member did the same in their allotted time for questioning. Lou Correa (D-CA), for example, said he was “beyond shocked” at the security revelations in the CSRB report and elsewhere.
Microsoft President Smith Pledges Action
Perhaps anticipating a rough reception from lawmakers, Smith struck a conciliatory tone in his
written and spoken testimony to the committee.
“Microsoft accepts responsibility for each and every one of the issues cited in the CSRB’s report,” Smith said. “Without equivocation or hesitation. And without any sense of defensiveness. But rather with a complete commitment to address every recommendation and use this report as an opportunity and foundation to strengthen our
cybersecurity protection across the board.”
Smith said the company is making cybersecurity part of senior executive bonus calculations and employee reviews as part of the its goal of “empowering and rewarding every employee to find security issues, report them, help fix them, and encourage broader learning from the process and the results. This requires that we incorporate this security work as an indispensable and integrated element in every aspect of the company’s engineering processes.”
[caption id="attachment_77142" align="alignnone" width="750"]

Microsoft President Brad Smith testifying before House Homeland Security Committee[/caption]
To that end, Smith said the company has added 1,600 more security engineers this fiscal year, “and we will add another 800 new security positions in our next fiscal year.”
Senior-level Deputy CISOs at Microsoft have been tasked with expanding “oversight of the various engineering teams to assess and ensure that security is ‘baked into’ engineering decision-making and processes.”
Smith said cyberattacks in general have become a massive problem: “the pace of attacks has increased to the point where there is now constant combat in cyberspace,” he said. “Not just every day, but literally every second. Microsoft alone detects almost 4,000 password-based attacks against our customers every second of every day.”
Microsoft Security Plans
Smith said Microsoft has mapped all 16 of the CSRB recommendations applicable to Microsoft “to ensure that we are addressing them” as part of the company’s Secure Future Initiative.
The company is “actively in the process of transitioning both our consumer and enterprise identity systems to a new hardened key management system that leverages hardware security modules for the storage and generation of keys. We are rolling out proprietary
data and corresponding detection signals at all places where tokens are validated. And we have made significant progress on Automated and Frequent Key Rotation, Common Auth Libraries, and Proprietary Data used in our token generation algorithm.”
Smith’s written testimony outlined six “pillars” for improving security:
Protect Identities and Secrets: Microsoft plans to implement and enforce “best-in-class standards across our infrastructure that manages identities and sensitive information such as passwords ('secrets'), to ensure that only the right people and applications access the right resources.”
Protect Tenants and Isolate Production Systems: The company pledges to “continuously validate isolation of production systems – including those upon which we operate the Microsoft Cloud.”
Protect Networks: Microsoft will “Continuously improve and implement best-in-class practices to protect Microsoft production networks.”
Protect Engineering Systems: The company said it will work to “Continuously improve our software supply chain and the systems that enable Microsoft engineers to develop, build, test, and release software, thereby protecting software assets and improving code security.”
Monitor and Detect Threats: This initiative calls for Microsoft to improve “coverage and automatic detection of ever evolving threats to Microsoft production infrastructure and services, accelerating actioning against those threats.”
Accelerate Response and Remediation: Speeding incident response and remediation is the final pillar, so “when we learn of
vulnerabilities in our offerings or our infrastructure, to be even more comprehensive and timely and better prevent exploitation of those vulnerabilities.”
Updated to reflect the delay in the Recall rollout.

 GrimResource YARA detection rule (source: Elastic Security Labs)[/caption]
“Defenders should leverage our detection guidance to protect themselves and their customers from this technique before it proliferates into commodity threat groups,” the researchers warned.
GrimResource YARA detection rule (source: Elastic Security Labs)[/caption]
“Defenders should leverage our detection guidance to protect themselves and their customers from this technique before it proliferates into commodity threat groups,” the researchers warned. 

 Source: Ransomware.live[/caption]
The other organization targeted by the ransomware group is
Source: Ransomware.live[/caption]
The other organization targeted by the ransomware group is  Source: Ransomware.live[/caption]
Until an official statement is released by the two firms, the facts behind the BlackBasta ransomware attack claim will likely remain elusive.
If BlackBasta's claims are proven true, the implications could be significant. The compromise of sensitive legal information and client data could have broad consequences, not only for the firms concerned but also for its clients and partners.
Source: Ransomware.live[/caption]
Until an official statement is released by the two firms, the facts behind the BlackBasta ransomware attack claim will likely remain elusive.
If BlackBasta's claims are proven true, the implications could be significant. The compromise of sensitive legal information and client data could have broad consequences, not only for the firms concerned but also for its clients and partners.







 Aaron Sterritt walks out of court. Source: Belfast Telegraph[/caption]
The first company targeted by the gang was Flowplay Inc., who had 75 million online gamers across the world in 2016, according to a
Aaron Sterritt walks out of court. Source: Belfast Telegraph[/caption]
The first company targeted by the gang was Flowplay Inc., who had 75 million online gamers across the world in 2016, according to a 






 Microsoft President Brad Smith testifying before House Homeland Security Committee[/caption]
To that end, Smith said the company has added 1,600 more security engineers this fiscal year, “and we will add another 800 new security positions in our next fiscal year.”
Senior-level Deputy CISOs at Microsoft have been tasked with expanding “oversight of the various engineering teams to assess and ensure that security is ‘baked into’ engineering decision-making and processes.”
Smith said cyberattacks in general have become a massive problem: “the pace of attacks has increased to the point where there is now constant combat in cyberspace,” he said. “Not just every day, but literally every second. Microsoft alone detects almost 4,000 password-based attacks against our customers every second of every day.”
Microsoft President Brad Smith testifying before House Homeland Security Committee[/caption]
To that end, Smith said the company has added 1,600 more security engineers this fiscal year, “and we will add another 800 new security positions in our next fiscal year.”
Senior-level Deputy CISOs at Microsoft have been tasked with expanding “oversight of the various engineering teams to assess and ensure that security is ‘baked into’ engineering decision-making and processes.”
Smith said cyberattacks in general have become a massive problem: “the pace of attacks has increased to the point where there is now constant combat in cyberspace,” he said. “Not just every day, but literally every second. Microsoft alone detects almost 4,000 password-based attacks against our customers every second of every day.”

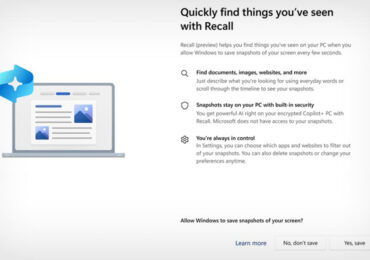



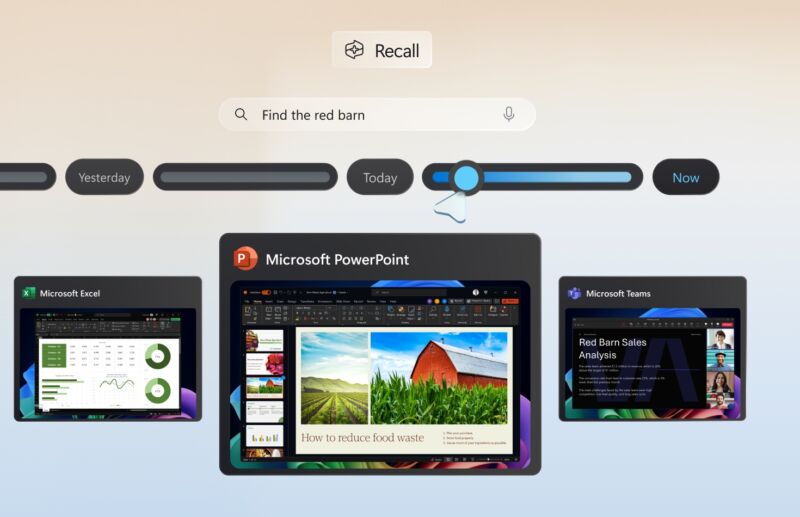

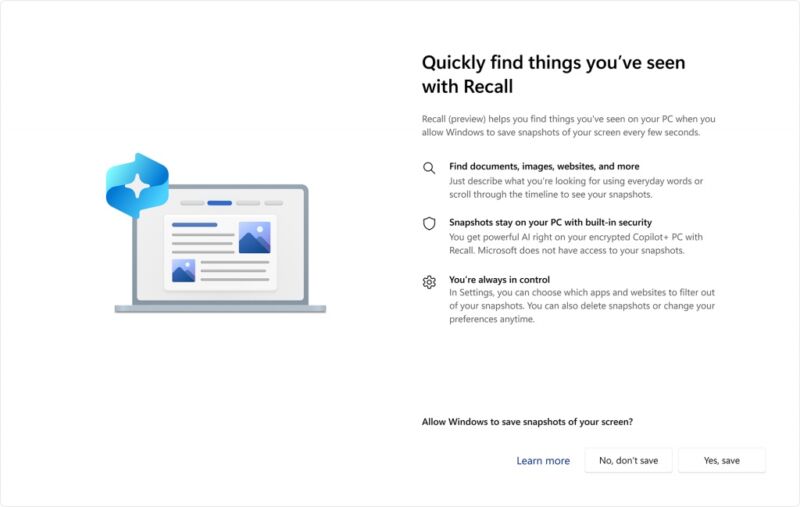

 Windows Recall opt-in screen (source: Microsoft)[/caption]
Enrollment in Windows Hello authentication will be required to enable Recall, he said, and “proof of presence is also required to view your timeline and search in Recall.”
Davuluri said Microsoft is also “adding additional layers of
Windows Recall opt-in screen (source: Microsoft)[/caption]
Enrollment in Windows Hello authentication will be required to enable Recall, he said, and “proof of presence is also required to view your timeline and search in Recall.”
Davuluri said Microsoft is also “adding additional layers of 



