CISA: Hackers Breached Chemical Facilities’ Data in January

Potential Data Compromised in Chemical Facilities' Targeting
CISA's investigation found no direct evidence of data exfiltration but indicated that the hackers might have accessed critical information such as site security plans, security vulnerability assessments (SVAs), and user accounts within CSAT. Additionally, "Top-Screen surveys," which detail the types and quantities of chemicals, their properties, and storage methods at facilities, might have been exposed. High-risk chemical facilities are mandated to submit SVAs outlining their critical assets, cyber and physical security policies, and an analysis of potential vulnerabilities. Other compromised documents could include details on cybersecurity measures, alarms and physical barriers in place at these facilities.CISA's Response and Recommendations
CISA has informed participants in the Chemical Facility Anti-Terrorism Standards (CFATS) program about the potential data exposure. Although no credentials were confirmed to be stolen, CISA advises those with CSAT accounts reset any identical business or personal passwords. They also recommend organizations using Ivanti products review a February advisory about recent vulnerabilities. The agency cannot directly notify individuals submitted for terrorist vetting under the CFATS Personnel Surety Program because it did not collect their contact information. However, identity protection services will be offered to those affected, specifically those vetted between December 2015 and July 2023.Investigation Findings
The breach was detected on January 26, when CISA discovered hackers installing tools on an Ivanti device. Further investigation revealed multiple accesses to the system over two days. Various departments within CISA and the Department of Homeland Security (DHS) were involved in the investigation, which confirmed no hacker access beyond the initial Ivanti device. Despite the absence of evidence for data exfiltration, the potential risk to numerous individuals and organizations categorized this intrusion as a "major incident" under the Federal Information Security Modernization Act (FISMA). CISA is setting up a call center to assist impacted individuals, although it is not yet operational. The agency did not comment on the perpetrators of the attack, but since 2020, CISA has cautioned organizations about state-sponsored hackers, including those linked to China, exploiting vulnerabilities in Ivanti products.Experts Say More Transparency Required
Roger Grimes, a data-driven defense evangelist at KnowBe4, lauded CISA's intent and the fact that it publicly accepted the hack but said a bit more transparency would have done no harm.
"I'm a big fan of CISA. I think they do wonderful work. Still, it would be useful to have better, full transparency," Grimes told The Cyber Express. "Was their Ivanti device exploited by an unpatched, but known vulnerability, or exploited by a 0-day? If they were exploited by a known vulnerability where a patch was available, which is more likely, why wasn't the patch installed? Was it simply due to the fact that the exploit happened faster than the patch could be applied? Was the patch missed? If the patch was missed, why? Or was it a 0-day, misconfiguration, or credential compromise?"
"This is not to embarrass CISA, but to learn why one of the best, most aggressive patch-pushing, cyber-defending organizations in the world got compromised," Grimes added. "Sharing what happened and why can help other organizations facing similar problems and challenges learn lessons.
"CISA is always pushing for other industries and vendors to be more transparent about their compromises so that we can all learn from the lessons and mistakes. I expect CISA to do the same and even lead by example when it's their infrastructure involved."



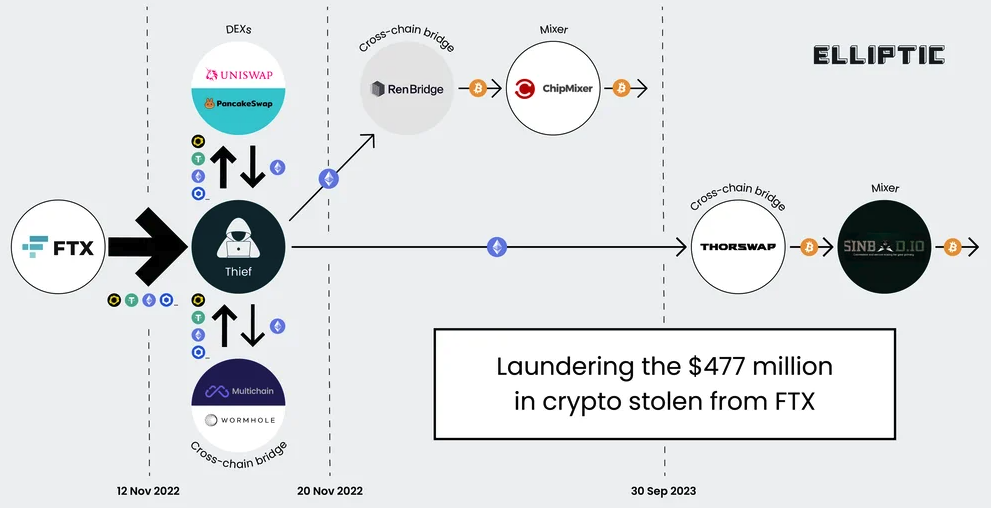
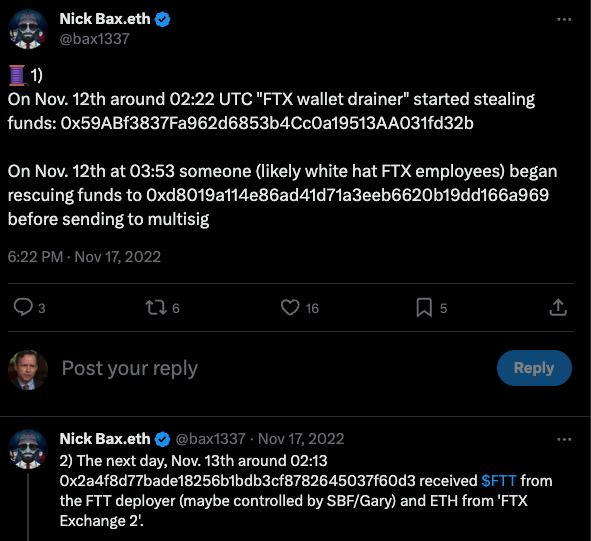
 Source: Chris Pashley's LinkedIn Post[/caption]
Source: Chris Pashley's LinkedIn Post[/caption]