Embattled Alzheimer’s Researcher Is Charged With Fraud

© Ilana Panich-Linsman for The New York Times

© Ilana Panich-Linsman for The New York Times

Chinese fast-fashion-cum-junk retailer “is a data-theft business.”
The post Temu is Malware — It Sells Your Info, Accuses Ark. AG appeared first on Security Boulevard.







 Source: X[/caption]
The breached data purportedly includes names of employees, 6,623 unique email addresses, their codes, date of birth, gender, policy name, relationships, dates of joining, effective dates, statuses, and entities.
To substantiate the claim, the threat actor 888 provided a sample of the data breach, which contains details of Credit Suisse employees in India.
[caption id="attachment_79025" align="alignnone" width="1362"]
Source: X[/caption]
The breached data purportedly includes names of employees, 6,623 unique email addresses, their codes, date of birth, gender, policy name, relationships, dates of joining, effective dates, statuses, and entities.
To substantiate the claim, the threat actor 888 provided a sample of the data breach, which contains details of Credit Suisse employees in India.
[caption id="attachment_79025" align="alignnone" width="1362"] Source: X[/caption]
The TA, however, did not provide a specific price for the sale of data and has requested potential buyers to quote a figure. The hacker commented that they are only accepting cryptocurrency as the mode of payment. More specifically, the hacker was open to payment on Monero (XMR), a digital currency renowned for its privacy and anonymity attributes. This method of payment is often utilized in illegal transactions to evade detection.
Despite these claims by the threat actor, a closer inspection reveals that the bank’s website is currently functioning normally, showing no signs of a security breach. The Cyber Express has reached out to the bank to verify the alleged cyberattack. As of now, no official statements or responses have been received, leaving the claims unverified.
Source: X[/caption]
The TA, however, did not provide a specific price for the sale of data and has requested potential buyers to quote a figure. The hacker commented that they are only accepting cryptocurrency as the mode of payment. More specifically, the hacker was open to payment on Monero (XMR), a digital currency renowned for its privacy and anonymity attributes. This method of payment is often utilized in illegal transactions to evade detection.
Despite these claims by the threat actor, a closer inspection reveals that the bank’s website is currently functioning normally, showing no signs of a security breach. The Cyber Express has reached out to the bank to verify the alleged cyberattack. As of now, no official statements or responses have been received, leaving the claims unverified.

 Source: X[/caption]
The threat actor claims to have accessed 1.2 TB of organization data, including accounting, budget, and financial data; contract data and NDAs; files from the CFO's computer; operational and business files; and email and PST archives. The group has also disclosed sensitive information such as the names, personal email addresses, and phone numbers of BBB’s CEO, vice president, chief accreditation officer, and chief activation officer.
The other organization that has allegedly fallen victim to the ransomware group is US Dermatology Partners. The organization, with a revenue of $213.7 Million, is one of the premier dermatology practitioners in the USA, caring for over two million patients annually.
[caption id="attachment_79002" align="alignnone" width="1259"]
Source: X[/caption]
The threat actor claims to have accessed 1.2 TB of organization data, including accounting, budget, and financial data; contract data and NDAs; files from the CFO's computer; operational and business files; and email and PST archives. The group has also disclosed sensitive information such as the names, personal email addresses, and phone numbers of BBB’s CEO, vice president, chief accreditation officer, and chief activation officer.
The other organization that has allegedly fallen victim to the ransomware group is US Dermatology Partners. The organization, with a revenue of $213.7 Million, is one of the premier dermatology practitioners in the USA, caring for over two million patients annually.
[caption id="attachment_79002" align="alignnone" width="1259"] Source: X[/caption]
The hackers claimed to have accessed 300 GB of organization data, including personal data, accounting and budget information, financial data, contract data and NDAs, and employee profiles.
Source: X[/caption]
The hackers claimed to have accessed 300 GB of organization data, including personal data, accounting and budget information, financial data, contract data and NDAs, and employee profiles.

 The hacker also posted details of call log samples which leaked sensitive information like mobile numbers of users, the date and duration of calls, and the amount charged for the call in Indian Rupees. The call log samples were being leaked in two sets: one for the month of May 2024 and another from 2020. This indicates that the data breach was a recent attack raising questions over the security checks in place at BSNL.
The hacker also posted details of call log samples which leaked sensitive information like mobile numbers of users, the date and duration of calls, and the amount charged for the call in Indian Rupees. The call log samples were being leaked in two sets: one for the month of May 2024 and another from 2020. This indicates that the data breach was a recent attack raising questions over the security checks in place at BSNL.
 The threat actor was selling the alleged stolen data for $5,000. The steep price tag could indicate the significant value of the stolen data which is sensitive. The Cyber Express has yet to verify the authenticity of the recent BSNL data breach and has contacted the organization for an official response. This article will be updated based on their response.
The threat actor was selling the alleged stolen data for $5,000. The steep price tag could indicate the significant value of the stolen data which is sensitive. The Cyber Express has yet to verify the authenticity of the recent BSNL data breach and has contacted the organization for an official response. This article will be updated based on their response.

 Source: X[/caption]
Source: X[/caption]

Enlarge / Dr. Peter Marks, Director of the Center for Biologics Evaluation and Research within the Food and Drug Administration on March 18, 2021 in Washington, DC. (credit: Getty | Susan Walsh)
The Food and Drug Administration (FDA) on Thursday announced expanded approval for a gene therapy to treat Duchenne muscular dystrophy (DMD)—despite the fact that it failed a Phase III clinical trial last year and that the approval came over the objections of three of FDA's own expert review teams and two of its directors.
In fact, the decision to expand the approval of the therapy—called Elevidys (delandistrogene moxeparvovec-rokl)—appears to have been decided almost entirely by Peter Marks, Director of the FDA's Center for Biologics Evaluation and Research.
Elevidys initially gained an FDA approval last year, also over objections from staff. The therapy intravenously delivers a transgene that codes for select portions of a protein called dystrophin in healthy muscle cells; the protein is mutated in patients with DMD. Last year's initial approval occurred under an accelerated approval process and was only for use in DMD patients ages 4 and 5 who are able to walk. In the actions Thursday, the FDA granted a traditional approval for the therapy and opened access to DMD patients of all ages, regardless of ambulatory status.

 Source: X[/caption]
The threat actor claimed to have carried out a cyberattack and had gained access to the data of 32 million Jollibee customers, including their names, addresses, phone numbers, email addresses and hashed passwords. The hacker also allegedly exfiltrated 600 million rows of data related to food delivery, sales orders, transactions and service details.
To support these claims, the TA included a sample in tabular data format accessible through spreadsheet programs like Microsoft Excel and Google Sheets.
While the exact details of the alleged data breach remains unclear, the potential impact on millions of customers is cause for concern.
Source: X[/caption]
The threat actor claimed to have carried out a cyberattack and had gained access to the data of 32 million Jollibee customers, including their names, addresses, phone numbers, email addresses and hashed passwords. The hacker also allegedly exfiltrated 600 million rows of data related to food delivery, sales orders, transactions and service details.
To support these claims, the TA included a sample in tabular data format accessible through spreadsheet programs like Microsoft Excel and Google Sheets.
While the exact details of the alleged data breach remains unclear, the potential impact on millions of customers is cause for concern.

The problems with passwords drive the interest to adopt newer authentication methods, like passkeys, a type of passwordless technology.
The post Criminals are Easily Bypassing Passkeys – How Organizations Can Stay Safe appeared first on Security Boulevard.

Location tracking service leaks PII, because—incompetence? Seems almost TOO easy.
The post Tile/Life360 Breach: ‘Millions’ of Users’ Data at Risk appeared first on Security Boulevard.
Notorious data leak site BreachForums appears to be back online after it was seized by law enforcement a few weeks ago.
At least one of BreachForums domains and its dark web site are live again. However, questions have been raised over whether it is a genuine attempt to revive the forums once again or set up as a lure by law enforcement to entrap more data dealers and cybercriminals.
The administrator of the new forum posts under the handle ShinyHunters, which is a name associated with the AT&T breach and others, and believed to be the main administrator of the previous BreachForums.
Yesterday, ShinyHunters posted a new dataset for sale that allegedly stems from Live Nation/Ticketmaster.
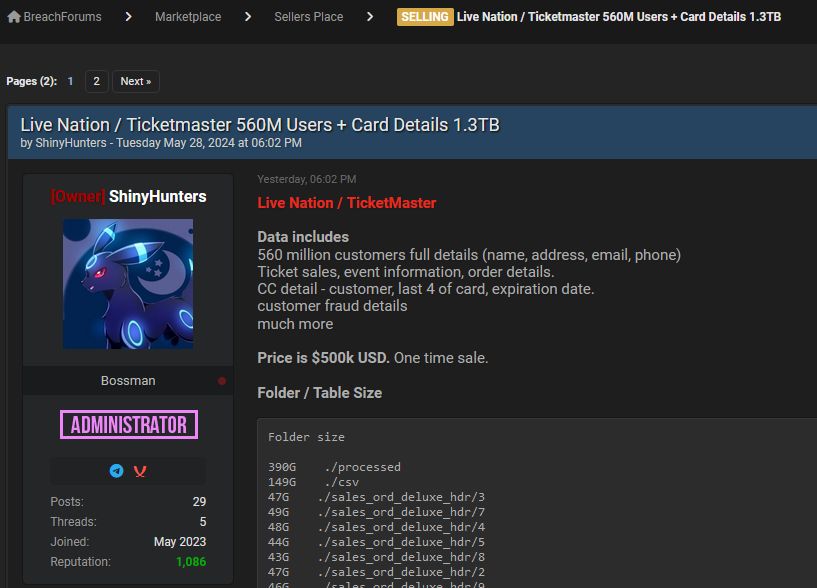
“Live Nation / Ticketmaster
Data includes
560 million customer full details (name, address, email, phone)
Ticket sales, event information, order details
CC detail – customer last 4 of card, expiration date
Customer fraud details
Much more
Price is $500k USD. One time sale.”
But, an avatar and a handle are easily copied, and there are a few things that raised our spidey-senses that something is up.
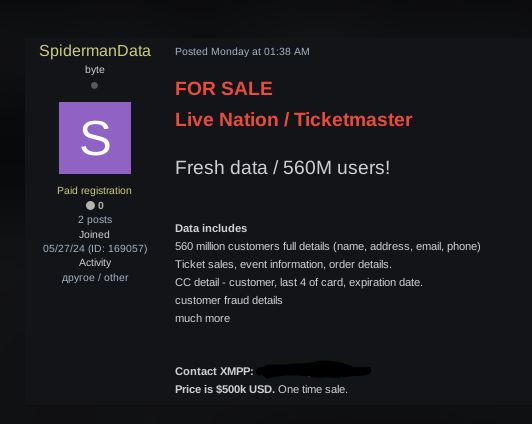
First, the data set was offered for sale on another dark web forum by a user going by SpidermanData with the exact same text.
Second, this data set seems way too big for its nature. Live Nation and Ticketmaster are big enough to be considered a monopolist, but 560 million users seems like a stretch.
After looking at the shared evidence, security researcher CyberKnow tweeted:
“While there is some new data in the shared evidence there is also old customer information, making it possibly this is a series of data jammed together.”
Third, a new feature is that visitors need to register before they can see any content. Why would the administrators change that?
And, last but not least, would the FBI let the cybercriminals regain control over the domains that easily? That would be quite embarrassing.
So, we dare conclude that this dataset’s goal is to generate some attention and act as a lure to let old forum users know that BreachForums is alive and kicking. But who is running the show, is the question that we hope to answer soon.
Stay tuned for updates on this developing story.
There are some actions you can take if you are, or suspect you may have been, the victim of a data breach.
Our Digital Footprint portal allows you to quickly and easily check if your personal information has been exposed online. Just enter your email address (it’s best to submit the one you most frequently use) to our free Digital Footprint scan and we’ll give you a report.
We don’t just report on threats – we help safeguard your entire digital identity
Cybersecurity risks should never spread beyond a headline. Protect your—and your family’s—personal information by using identity protection.
Across America, survivors of domestic abuse and stalking are facing a unique location tracking crisis born out of policy failure, unclear corporate responsibility, and potentially risky behaviors around digital sharing that are now common in relationships.
No, we’re not talking about stalkerware. Or hidden Apple AirTags. We’re talking about cars.
Modern cars are the latest consumer “device” to undergo an internet-crazed overhaul, as manufacturers increasingly stuff their automobiles with the types of features you’d expect from a smartphone, not a mode of transportation.
There are cars with WiFi, cars with wireless charging, cars with cameras that not only help while you reverse out of a driveway, but which can detect whether you’re drowsy while on a long haul. Many cars now also come with connected apps that allow you to, through your smartphone, remotely start your vehicle, schedule maintenance, and check your tire pressure.
But one feature in particular, which has legitimate uses in responding to stolen and lost vehicles, is being abused: Location tracking.
It’s time car companies do something about it.
In December, The New York Times revealed the story of a married woman whose husband was abusing the location tracking capabilities of her Mercedes-Benz sedan to harass her. The woman tried every avenue she could to distance herself from her husband. After her husband became physically violent in an argument, she filed a domestic abuse report. Once she fled their home, she got a restraining order. She ignored his calls and texts.
But still her husband could follow her whereabouts by tracking her car—a level of access that Mercedes representatives reportedly could not turn off, as he was considered the rightful owner of the vehicle (according to The New York Times, the husband’s higher credit score convinced the married couple to have the car purchased in his name alone).
As reporter Kashmir Hill wrote of the impasse:
“Even though she was making the payments, had a restraining order against her husband and had been granted sole use of the car during divorce proceedings, Mercedes representatives told her that her husband was the customer so he would be able to keep his access. There was no button she could press to take away the app’s connection to the vehicle.”
This was far from an isolated incident.
In 2023, Reuters reported that a San Francisco woman sued her husband in 2020 for allegations of “assault and sexual battery.” But some months later, the woman’s allegations of domestic abuse grew into allegations of negligence—this time, against the carmaker Tesla.
Tesla, the woman claimed in legal filings, failed to turn off her husband’s access to the location tracking capabilities in their shared Model X SUV, despite the fact that she had obtained a restraining order against her husband, and that she was a named co-owner of the vehicle.
When The New York Times retrieved filings from the San Francisco lawsuit above, attorneys for Tesla argued that the automaker could not realistically play a role in this matter:
“Virtually every major automobile manufacturer offers a mobile app with similar functions for their customers,” the lawyers wrote. “It is illogical and impractical to expect Tesla to monitor every vehicle owner’s mobile app for misuse.”
Tesla was eventually removed from the lawsuit.
In the Reuters story, reporters also spoke with a separate woman who made similar allegations that her ex-husband had tracked her location by using the Tesla app associated with her vehicle. Because the separate woman was a “primary” account owner, she was able to remove the car’s access to the internet, Reuters reported.
Location tracking—and the abuse that can come with it—is a much-discussed topic for Malwarebytes Labs. But the type of location tracking abuse that is happening with shared cars is different because of the value that cars hold in situations of domestic abuse.
A car is an opportunity to physically leave an abusive partner. A car is a chance to start anew in a different, undisclosed location. In harrowing moments, cars have also served as temporary shelter for those without housing.
So when a survivor’s car is tracked by their abuser, it isn’t just a matter of their location and privacy being invaded, it is a matter of a refuge being robbed.
In speaking with the news outlet CalMatters, Yenni Rivera, who works on domestic violence cases, explained the stressful circumstances of exactly this dynamic.
“I hear the story over and over from survivors about being located by their vehicle and having it taken,” Rivera told CalMatters. “It just puts you in a worst case situation because it really triggers you thinking, ‘Should I go back and give in?’ and many do. And that’s why many end up being murdered in their own home. The law should make it easier to leave safely and protected.”
Though the state of California is considering legislative solutions to this problem, national lawmaking is slow.
Instead, we believe that the companies that have the power to do something act on that power. Much like how Malwarebytes and other cybersecurity vendors banded together to launch the Coalition Against Stalkerware, automakers should work together to help users.
Fortunately, an option may already exist.
When the Alliance for Automobile Innovation warned that consumer data collection requests could be weaponized by abusers who want to comb through the car location data of their partners and exes, the automaker General Motors already had a protection built in.
According to Reuters, the roadside assistance service OnStar, which is owned by General Motors, allows any car driver—be they a vehicle’s owner or not—to hide location data from other people who use the same vehicle. Rivian, a new electric carmaker, is reportedly working on a similar feature, said senior vice president of software development Wassym Bensaid in speaking with Reuters.
Though Reuters reported that Rivian had not heard of their company’s technology being leveraged in a situation of domestic abuse, Wassym believed that “users should have a right to control where that information goes.”
We agree.
We don’t just report on threats—we remove them
Cybersecurity risks should never spread beyond a headline. Keep threats off your devices by downloading Malwarebytes today.